@Sedo @namesilo nwx.com listed for sale at $15,750 it's been stolen, NameSilo you are the new registrant I spoke to the owner it was stolen from his mydomain account and transferred to you, this name is stolen.
You are using an out of date browser. It may not show this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.


Watch
More options
Show metrics- Impact
- 448
Received query from who? And what was the query about?
What was the outcome? ... did they award the domain to you, or was it returned?
they had locked domain for 2 days,
and after investigation they awarded domain to me. and unlocked them as well.
I had to send mail to godaddy support..
Very first time, i had doubt that there might be stolen domain, but when dispute came, i contacted seller, and she told me to return money, if domain are not removed from dispute.
but when it got resolved from Godaddy, i denied for refund, and i found that domains are not stolen...
"There might be a possibility that seller wanted to get trust by selling some domains, and preparing for bigger scam..."
"Unless old owner file dispute, we can not tag every domain as stolen one.., but better to file paypal claim for disputed domain...."
- Impact
- 12,102
they had locked domain for 2 days,
and after investigation they awarded domain to me. and unlocked them as well.
I had to send mail to godaddy support..
Very first time, i had doubt that there might be stolen domain, but when dispute came, i contacted seller, and she told me to return money, if domain are not removed from dispute.
but when it got resolved from Godaddy, i denied for refund, and i found that domains are not stolen...
Thanks for the clarification.
I've never encountered this before. Just so I understand, GoDaddy sent you an email notifying you the domains had been locked and were under investigation?
Then they finished their investigation, and awarded you the domains?
For educational purposes, would you mind sharing those emails?
"There might be a possibility that seller wanted to get trust by selling some domains, and preparing for bigger scam..."
This is possible. But at the same time, should the seller have sold domains they legitimately registered, there may be a footprint leading back to their identity. As such, a scammer could have motive to only deal in stolen domains.
All three domains being sold in the below screenshot have a longstanding digital footprint attached to a John Makowski of Maryland using a @comcast.net email.
Mr. Makowski could have legitimately sold them, and Paty could have legitimately acquired, and sold them in effort to build trust. But given the current shenanigans, there could be more to this. Might be best to contact Mr. Makowski and see what (if anything) can be confirmed.
Last edited:
Can confirm that both appear to be the same person (not just the same IP address).
The possibility of either account being compromised shouldn't be ruled out, though there is circumstantial evidence suggesting that isn't likely to be the case.
This is a good opportunity for a PSA: If your password here is the same as your password anywhere else, change it. You need a password manager. If you're doing business online, it's not optional. It is quite possibly the single best step you can take toward security your online assets. If you can remember your password, it's a bad password.
Some reputable password managers, in no particular order:
Additional security tips:
- SMS doesn't count as 2FA. It's nearly useless. I don't even know why websites still offer this; it's security theater and offers no significant protection. All it does is inconvenience you. Don't even add SMS as a backup option; you're completely eliminating the benefits of 2FA when you do that.
- OATH is your best option for 2FA. Typically this involves installing an app on your phone and taking a picture of a funky-looking QR code. Google Authenticator and Authy are both popular apps for this purpose. This is what NamePros offers and recommends.
- If you find 2FA codes inconvenient, consider getting a YubiKey. Not all websites support them, but the number is growing, and NamePros plans to support them in the near future. The cheap blue one is all most people need. I linked to the two-pack, as it's a good idea to have a backup.
- When choosing security questions and answers, don't use real answers. Generate random passwords in your password manager and use those instead. Hackers are better at figuring out the real answers than you are at remembering them.
Thanks for the post, why does SMS not count for 2FA?
Secondly I never use a password manager because I always thought that was the hacker goldmine if one of them get hacked, your thoughts on that Paul.
Thank you.
Asset Profit
Established Member
- Impact
- 25
I sold a Blog on Flippa once and they guy was happy after I catered to him post sale. Then he asked me for positive rating. Minutes after that he filed a dispute with Paypal saying he did not get his PLAYSTATION? It almost worked if not for all the evidence I had including his laughing about his own scam in an email to me.
I think we need a Resource we can all refer to on the dangers of scammers and the experiences perhaps to learn from. Of course a scammer would also read it and make the adjustments haha.
I think we need a Resource we can all refer to on the dangers of scammers and the experiences perhaps to learn from. Of course a scammer would also read it and make the adjustments haha.
- Impact
- 5,938
The person selling at Sedo is in Mexico. I have a bad feeling it is a certain NP member previously selling stolen names, but always claiming his innocence. Better not mention names...
Hi,
I don't get it, why better not to mention names?
Thanks
- Impact
- 448
Every guy who is selling stolen names are not thief always..I really would like to know who that person is, "previously selling stolen names".
I understand you don't want to mention it, perhaps its off topic too..
Thanks
some times he/she might be victim also..
there is a possibility that previous owner have stolen name from original one...
So better not to disclose anyone's name until its proven..
- Impact
- 5,623
I purchased an LLL.net from this person. I did do my due diligence on the name as best I could. I required the auth code and transfer prior to paying. It went smooth.
A day later, I received a contact via whois privacy from a gentleman in North Carolina. He noticed his email stopped working. Long story short, he has owned the domain for over 20 years. His domain account was apparently hacked and both his password and secret questions were changed. He is still trying to access his domain account.
I have initiated a paypal dispute. Obviously I can't keep the mans domain. It's stolen property.
I alerted NP mgmt, and they apparently have closed the user's account.
What a shame.
Wow. I wonder how all these domains are being stolen.
- Impact
- 47,110
- Impact
- 47,110
- Impact
- 1,792
They are being stolen through some form of hacking. A person doing the hack can be in any country in the world. As we can see here they posed as a member to gain our confidence, support and comfort and to also use us as a customer base. Most of our members here always do their due diligence when transacting a sale, however we see in this incident that hackers do find ways to slip through the cracks.
Hacking can be impeccably easy, at least some forms of it. Always have long and mixed passwords, always.
- Impact
- 1,140
- Impact
- 12,102
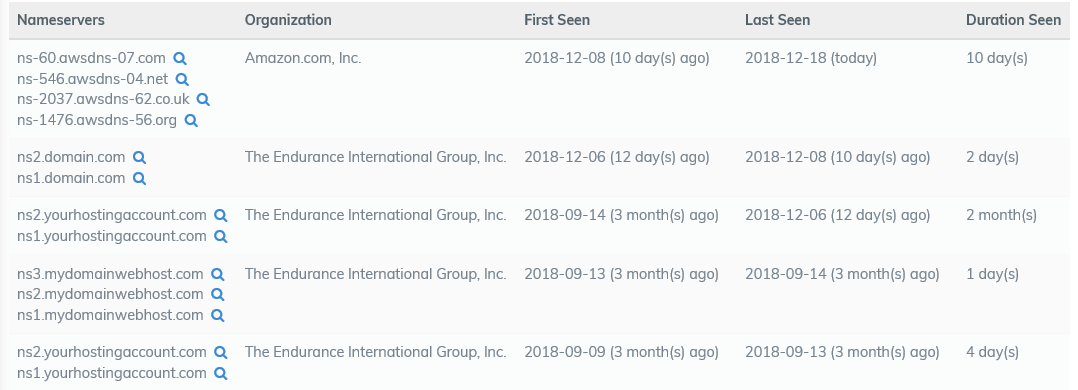
There was a NS update between 06-12-2018 to 08-12-2018
Something I'm wondering...
... Could the domain have been pushed to another domain.com affiliated registrar prior to being transferred to Namesilo?
According to SecurityTrails.com, the NameServers were changed to ns1.domain.com on or around December 6th. There is no record on SecurityTrails of the nameservers being changed to ns1.domain.com within the last 10 years; it appears to be a first.
I believe the default nameservers for MyDomain.com is ns1.mydomain.com. Whereas the default nameservers for Domain.com is NS1.domain.com.
... hence my thinking, that the domain may have been pushed from mydomain.com to another domain.com affiliated registrar prior to being transferred out. Not sure if that would be reflected in WHOIS updates to confirm or deny.
Just a thought.
Last edited:
@alcy Pushing domains between Domain.com, MyDomain.com, Netfirms and Dotster is possible. I've done it many times in the past. You need to have the details of both accounts and it involves a regular push as well as asking them to change the RSP (RSP stands for Registered Service Provider, if I'm not mistaken) to the new registrar. When they don't do that (or say they did but didn't because... well... often they're incompetent and have no idea what they're doing)- the domain is still technically in the first registrar even after the push is done and can't be controlled from the new registrar until the RSP is changed.
yes it can get quite complex... especially with the followup RSP changes etc.. and as you put it, incompetent reps outnumbering the competent ones...
however, the fact remains that it cannot be done on your own and needs support call.. or chat... whether its a mydomain to mydomain push... or mydomain to affiliated registrar.
cheers
- Impact
- 3,890
Weird. I have dealt with AlejandroGarcia in the past dating back several years and he has strong trade reviews. I wonder what is going on here...
Brad
See this one:
https://www.namepros.com/threads/stolen-four-letter-names.1071424/
Last edited:
- Impact
- 47,110
- Impact
- 448
Thanks for the clarification.
I've never encountered this before. Just so I understand, GoDaddy sent you an email notifying you the domains had been locked and were under investigation?
Then they finished their investigation, and awarded you the domains?
For educational purposes, would you mind sharing those emails?
This is possible. But at the same time, should the seller have sold domains they legitimately registered, there may be a footprint leading back to their identity. As such, a scammer could have motive to only deal in stolen domains.
All three domains being sold in the below screenshot were previous owned by a John Makowski of Maryland using a @comcast.net email.

Mr. Makowski could have legitimately sold them, and Paty could have legitimately acquired, and sold them in effort to build trust. But given the current shenanigans, there could be more to this. Might be best to contact Mr. Makowski and see what (if anything) can be confirmed.
@PatyGMar told me that she purchased from person having paypal id *****@comcast.net
Another possibility is the systematically planned scam, where she made some evidance by making fake deals on her own paypal, and domain transferred accounts more than one time...
So that she can easily misguide latest registrar, and paypal also. by providing proof that she has purchased domain from xyz person. (she might be trying to prove herself as victim..)
if registrars are changed more than one time, then there might be a possibility that they will not easily respond ownership disputes, unless UDRP case filed...
Because I don't know for sure if it is the person I suspect it is.
I really would like to know who that person is, "previously selling stolen names".
I understand you dont want to mention it, perhaps its off topic too..
Thanks
BestDomains2828
Restricted (Market)
- Impact
- 65
We need proves before jumping to conclusions.
BestDomains2828
Restricted (Market)
- Impact
- 65
How can he stolen all this names maybe this guy got a virus that is working for him.
They are being stolen through some form of hacking. A person doing the hack can be in any country in the world. As we can see here they posed as a member to gain our confidence, support and comfort and to also use us as a customer base. Most of our members here always do their due diligence when transacting a sale, however we see in this incident that hackers do find ways to slip through the cracks.Wow. I wonder how all these domains are being stolen.
WOW!! That hacker has been a very busy Domain Name Thief....Add the following to the list:
BCI.ORG
LGM.ORG
PVN.ORG
With that amount of domain names being linked to a hacked account should warrant all the registries attached to these domain names to work together with the possibility of a law enforcement investigation....There's about 125 more linked to that account; I only shared the LLL kind after verifying odd changes in ownership. They all have in common previous yahoo/AOL/Comcast etc. accounts. Others are linked to domains that dropped, and re-registered - a common domain hijacking technique.
Something I'm wondering...
... Could the domain have been pushed to another domain.com affiliated registrar prior to being transferred to Namesilo?
According to SecurityTrails.com, the NameServers were changed to ns1.domain.com on or around December 6th. There is no record on SecurityTrails of the nameservers being changed to ns1.domain.com within the last 10 years; it appears to be a first.
I believe the default nameservers for MyDomain.com is ns1.mydomain.com. Whereas the default nameservers for Domain.com is NS1.domain.com.
... hence my thinking, that the domain may have been pushed from mydomain.com to another domain.com affiliated registrar prior to being transferred out. Not sure if that would be reflected in WHOIS updates to confirm or deny.
Just a thought.
afaik u cant push between mydomain dotster netfirms etc
- Impact
- 12,102
not all reps are created equal. proof is in the fact that I was told exact opposite by another rep a while back when I wanted to do that.
Sounds like you had a bad rep. Ha. I think I remember pushing a domain from a domain.com affiliate to another domain.com affiliate in the past. But couldn't remember for sure. The chat with the rep confirmed it.
pushes are hard even mydomain to mydomain. cause you always have to call them or chat. u cannot do it yourself. then even when u call them, there are 2 ways to do it. and one of them involves knowing the secret accnt question of new owner.
I wonder if this 'secret accnt question' method works with MyDomain.com to Domain.com pushes. Or if it would have required assistance from support.
But back to the topic... I'm wondering if:
The alleged thief pushed the domain to their (or somebody else's) Domain.com (or affiliate site) account prior to transferring to Namesilo.
Not sure how (if) transfer locks (from MyDomain.com to Domain.com) would effect this.
Similar threads
8 replies
1K views
- Poll
12 replies
1K views
0 replies
316 views
3 replies
221 views
3 replies
369 views
Latest news
-
Beware of Sharks
- 20 replies
- Chris Hydrick
-
1Money.com Sold For $40,000 USD At Atom
- 48 replies
- silentg
New posts
-
Copilot - Showcase Thread
- 19 posters
- Kyle Tully
-
UGPQ.COM Start:100$
- Post by Ebizcard
Polls of interest
-
Best industry prefix?
- 20 replies
- 43 voters
-
Which is the best price?
- 62 replies
- 177 voters
-
What non .com extensions have you sold in 2024?
- 42 replies
- 166 voters
Popular this week
-
Beware of greedy member
- 12 points
- 197 replies
-
Sold 3L Domain on SEDO for 6 digit USD - Buyer not willing to pay
- 9 points
- 84 replies
-
I bid on a domain with a huge premium renewal at GD auction, by mistake.
- 15 points
- 49 replies
-
The .xyz registry seems quite influential
- 2 points
- 44 replies
-
Beware of Sharks
- 23 points
- 20 replies
Popular this month
-
Beware of greedy member
- 12 points
- 197 replies
-
HSTF.com: Seller gets questioned about value, raises price
- 8 points
- 90 replies
-
Changes coming to GoDaddy Auctions
- 7 points
- 78 replies
-
Squadhelp is now "atom"
- 13 points
- 72 replies
-
Sold 3L Domain on SEDO for 6 digit USD - Buyer not willing to pay
- 9 points
- 84 replies





