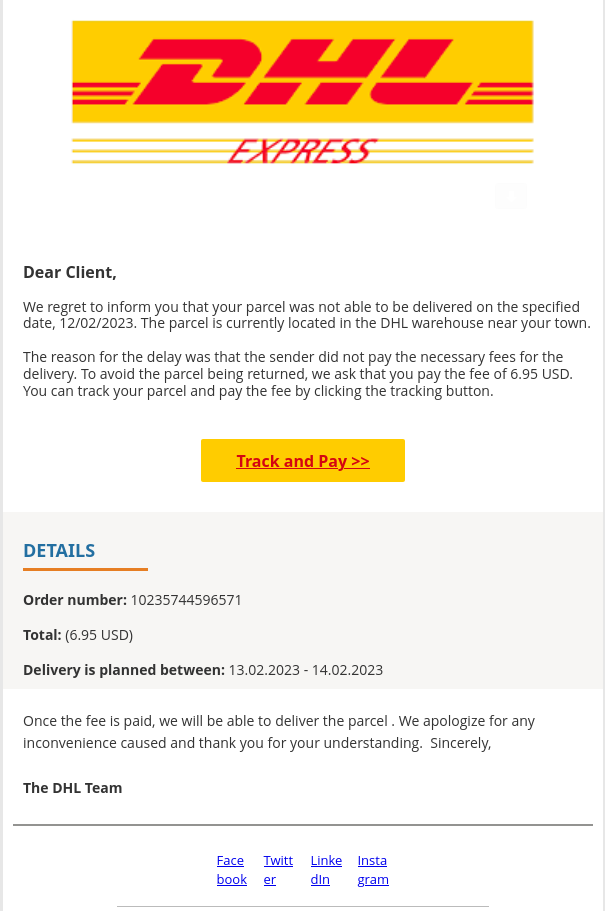
I hope I cleaned it up properly...
Delivered-To:
[my_mail]
Received: by 2002:a0c:d7d1:0:b0:534:7395:29d9 with SMTP id g17csp2940914qvj;
Sun, 12 Feb 2023 13:25:38 -0800 (PST)
X-Received: by 2002:a81:dc05:0:b0:52f:aab:5f71 with SMTP id h5-20020a81dc05000000b0052f0aab5f71mr3056322ywj.17.1676236897621;
Sun, 12 Feb 2023 13:21:37 -0800 (PST)
X-Google-Smtp-Source: AK7set/Y4XLx6CUK4OPxgJoIyt2DYAR+8D4ffd9SYC4vUjctrlsNbeaVzVErxRFqkbrLcN6ntkhJ
X-Received: by 2002:a81:dc05:0:b0:52f:aab:5f71 with SMTP id h5-20020a81dc05000000b0052f0aab5f71mr3056291ywj.17.1676236896577;
Sun, 12 Feb 2023 13:21:36 -0800 (PST)
ARC-Seal: i=1; a=rsa-sha256; t=1676236896; cv=none;
d=google.com; s=arc-20160816;
b=vwjrJ7FGyVmDEbg1vM/FC69WX8ryfO2kfsjVQg01oxJ2OuluO9plzeu2HTFIPKZYbc
Re8Jjxa76XVwTNIW6hAn1cAQfqpDso49LpRykpLglpZvOva6lG+5wkbZN6zXEMKFLUPJ
wBhDXsDPsFT+7f/AFjqitOq8ITRyZzlB0fFsyMP4BdartI5UW8dEqKhN3YamLND1hvUY
GwJrjTP9QGk/yBH11Ibn35iGk1X73oEAe9o40lu3g2yCWypT4t+SLSwlWCkrg7sTIv9r
5rqdHRpg9oCB7LzlXQ7NdQa9imjyU/+oXcqFvfj5pN2GoZGMM7dYiHXsbu14/Orx3aon
EtWA==
ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816;
h=to:reply-to:message-id:subject:mime-version:list-unsubscribe:from
:feedback-id:date:dkim-signature;
bh=5MLgTLrZB0u3RqAQCStwUI5dGjMMNfLn7ZSO3geJAnk=;
b=Wt2rGZotauheFnx5RaB4CGAKO1pYT9SXoyDaaoXuFk9/y1Wu2iKuOD3dS1gkkBaeVA
jrXFdiSo2laJs1uzrOs2I2Au3DVGC1vBjrPm7JEZe7o5tRPrLn4e64Ipvs1+nV68iUOc
oRUNa+2RwKyUCr6uEbB/l3v34Z46ECY4ZUsGIzMLoBuELiDWKd/5rYqMYTpoFCutEtmx
X1qbRjgvasCY+1CFPJo9nnwsF49HOD5wZ3ZsJNiE7weFFKFZtT0ZJSUCTHYcbwAI62Pw
xFAQ9xWyLL4UdjjwQEALwuMHsADjKrmZJTqfQ2+4ilqADrzjmqU3hPA+7LVUFNkFRfmY
B/Ow==
ARC-Authentication-Results: i=1; mx.google.com;
dkim=pass
[email protected] header.s=s1 header.b=ythgTo4+;
spf=pass (google.com: domain of bounces+4793763-779e-
[my_mail]@mailserviceemailout1.namecheap.com designates 167.89.64.95 as permitted sender) smtp.mailfrom="bounces+4793763-779e-
[my_mail]@mailserviceemailout1.namecheap.com";
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=namecheap.com
Return-Path: <bounces+4793763-779e-
[my_mail]@mailserviceemailout1.namecheap.com>
Received: from o6.mailservice.namecheap.com (o6.mailservice.namecheap.com. [167.89.64.95])
by mx.google.com with ESMTPS id q132-20020a815c8a000000b004fd32b6075dsi12268336ywb.116.2023.02.12.13.21.36
for <
[my_mail]>
(version=TLS1_3 cipher=TLS_AES_128_GCM_SHA256 bits=128/128);
Sun, 12 Feb 2023 13:21:36 -0800 (PST)
Received-SPF: pass (google.com: domain of bounces+4793763-779e-
[my_mail]@mailserviceemailout1.namecheap.com designates 167.89.64.95 as permitted sender) client-ip=167.89.64.95;
Authentication-Results: mx.google.com;
dkim=pass
[email protected] header.s=s1 header.b=ythgTo4+;
spf=pass (google.com: domain of bounces+4793763-779e-
[my_mail]@mailserviceemailout1.namecheap.com designates 167.89.64.95 as permitted sender) smtp.mailfrom="bounces+4793763-779e-
[my_mail]@mailserviceemailout1.namecheap.com";
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=namecheap.com
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=namecheap.com; h=content-type:from:list-unsubscribe:mime-version:subject:reply-to:to: cc:content-type:from:subject:to; s=s1; bh=5MLgTLrZB0u3RqAQCStwUI5dGjMMNfLn7ZSO3geJAnk=; b=ythgTo4+iQ/nQOitKZGKF28zU6G9lG8+FsJ/NRZ/QXINc8XV5jDxHBXf4vWQjhDzu8xh EjXnml9zYCNktsRYA2kNosXZaeCJPNDUgaDh3hD81YCueLwazlffCCXDEbjmjc7wk0TZgk qu76uksj2q8Sd8n+1j0NDr16LOV0Q0h7jh/V4hRbg8ffiDmtol42IOOEX4h1V+AECpYcrV a4Z3q10/72Gf3XClDeMBkV8spyjs7lG8JyuPVZsy5PIMfGSdxA4ODZav4tPgOvUzS4fY5P MYkTPyWDXyzzflgeXWQuK0+IF/21xOVeQsoEXOc8e1EMXSVGUP5XvTBg0Uen9O9g==
Received: by filterdrecv-b79bb7454-xcf6j with SMTP id filterdrecv-b79bb7454-xcf6j-1-63E9585F-68
2023-02-12 21:21:35.774950246 +0000 UTC m=+181305.375421437
Received: from NDc5Mzc2Mw (unknown) by geopod-ismtpd-5-1 (SG) with HTTP id iMbMpeRzStOHPFrYXY7ilw for <
[my_mail]>; Sun, 12 Feb 2023 21:21:35.707 +0000 (UTC)
Content-Type: multipart/alternative; boundary=f0f40b2bef6c62308fe702efeef447e1b23e2fbac9576460ad841833ad94
Date: Sun, 12 Feb 2023 21:21:35 +0000 (UTC)
Feedback-ID: 8288221:6168579:9774:iterable
From: "contact ." <
[email protected]>
List-Unsubscribe: <
https://links.namecheap.com/e/encryptedUnsubscribe?_r=9a766a4fa5294d089b01463bac20344b&_s=685fbf8d22a8421a95c168e93916e61f&_t=LJxzL8ZXnPxXCE_Kdn_vUmnC7fdvIr9qcVldWW2CqyZAfKw0X0CW4DhaGdQ1b8wXr-ibEoEvd04aU8jOeqFulcsXFGISKh7l_--Z6tE2A5Y=>,<mailto:
[email protected]>
Mime-Version: 1.0
Subject: MetaMask : Your wallet is about to be suspended
X-Campaign-ID: 6168579
X-Message-ID: 685fbf8d22a8421a95c168e93916e61f
Message-ID: <iMbMpeRzStOHPFrYXY7ilw@geopod-ismtpd-5-1>
Reply-To:
[email protected]
X-SG-EID: Sf/6gCYo6POogvTNeXQAUzuhmXXiY87VJrtPmjowdxcnfIoiiBzj+ETkhZGZDH6sNJMxo5N6KSgz1KVpBNNeXyVTYMIc/872sN3zsHmg6OTpcF48786LQ9oosrBa7X7eZUH1vRFT99T7UY+psJX4VDmFrCCdv8uhTvriG5RKEXtURiWQ/G6H76FR+DNWtVOb8yeQMRBYeJclrEFpqGGUS8b5nV0MQ81knBl8jngQJqU=
X-SG-ID: N2C25iY2uzGMFz6rgvQsb8raWjw0ZPf1VmjsCkspi/IARr5ApfQLGQYXi0KvHQ0z32Z/Xww8RCO+g+UQxQyQwD8nqfalxxxSXPrzzNr3pDyUfT2Mjz/Rg7yupzSi4u2IkbJGO7iOjw2ujQBua7la45RNbNYx+HESYUWPZfz9Jwtan4IT2ZWk0TFl6bxL6fyxhfcLb7GOGBYIl95ttL4aWg==
To:
[my_name] <
[my_mail]>
X-Entity-ID: nYXv3xAQEE15JmfKP56ELQ==