But the versions of reality are quite distinct. Either Mr. Gargiulo is mistaken or Mr. Dikian is a thief.
Which reality do you believe to be more likely, and why?
Does the answer depend on if Mr. Gargiulo was talking to the real Mr. Dikian of
[email protected], or as long as the emails did in fact come from
[email protected], then there is no way Mr. Gargiulo can be mistaken? Or is it, as mentioned earlier in this thread by
@Embrand that vitcims of hacked emails/identity fraud shouldn't be held responsible?
I don't think I read in Mr. Dikians response an admission that any of his email addresses were improperly authorized. Though, Mr. Dikian denied receiving March 8th emails to
[email protected] or
[email protected]. Mr. Dikian also denied sending a respond from those emails. However, Mr Dikian admitted to notifying the plaintiff by email from
[email protected] on May 11th.
So if it's determined emails weren't spoofed, and emails were sent to/from
[email protected] without the real Mr. Dikians knowledge, it seems for Mr. Gargiulo to be mistaken, then Mr Dikians accounts or emails would have to had been accessed by somebody (likely a bitcoin thief?) without the real Mr. Dikians authorization?
If Mr Dikian's yahoo account was accessed without his authorization, I assume/hope the real Mr. Dikian already:
-- looked at his yahoo account activity:
https://login.yahoo.com/myaccount/activity
-- downloaded his Yahoo history:
https://yahoo.mydashboard.oath.com/
-- checked to see if any filters were set/left in his account:
https://mail.yahoo.com/d/settings/7
-- checked to see if any email addresses were set/left to block:
https://mail.yahoo.com/d/settings/8
Further, if Mr. Dikians email or accounts were indeed hacked, what could have led to somebody gaining access to his accounts? Does Mr. Dikian have a history of account hacks leading to stolen domains or anything similar... or why now?
I found five email addresses based on historical WHOIS records that look (
assumed, not confirmed) to have some type of connection to a George Dikian. (1)
[email protected] (2)
[email protected] (3)
[email protected] (4)
[email protected] (5)
[email protected]
Besides some historical WHOIS Dikian connection, what else do these
5 email addresses have in common?
All 5 were listed as being pwned in the September 2021 Epik hack which according to HaveIBeenPWNED.com cite the compromised data as:
Email addresses, Names, Phone numbers, Physical addresses, Purchases.
As mentioned earlier, Intermediar.com trustPilot account was verified via "Contact details Google My Business account verified and synced" on
January 2022.
It appears, if Epik had George Dikians physical address on file, then it may likely have been leaked. Not sure if that, in combination of other data was used to gain unauthorized access to Dikian accounts, but some may find it interesting to note if a epik leaked Dikian address was different than the L.A. address VPN initially listed for Dikian in the California civil summons.
namePros member
@.X. appeared to
report that his data wasn't just stolen from epik, but somebody had used his home address, and committed a crime with it.
...my data wasn’t just stolen from Epik, someone used my home address as their own address , that person committed a crime using my home address, and I got a call from the BIG men.
Now, there's no direct indication that the September 2021 epik hack led to Mr. Dikians account(s) being hacked. Checking email addresses across HaveIBeenPWNED.com is just one initial step to take when begining to question how an account may have been hacked/socialEngineered/accessedWithOut authorization. But, notable in this instance, the 5 email addresses I found that looked like it could have a George Dikian domain connection all appeared to have been pwned in the 2021 epik hack.
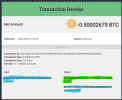
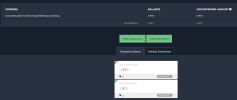
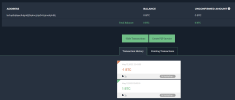
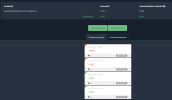
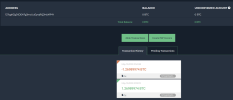
Lastly, since we are talking about missing bitcoin, there is a ledger of it being moved. I'm not a crypto guy, but some basic internet search seem to reveal wallet movement. IDK how to make much sense of that data, but if nothing else, I feel publishing those wallet addresses to this thread or elsewhere may leave a internet record which somebody by have knowledge of now, or in a cached future. Below is the wallet address provided to VPN by somebody alleging to be George Dikian, in case any crypto sleuths want to try to make sense of what happened to the BTC:::
36. On April 24, 2022, Dikian provided his Bitcoin wallet address to VPN in order for VPN to make the $250,000 payment once Intermediar confirmed completion of the transaction. Dikian provided the following Bitcoin wallet address: bc1qymcdwgqde47qxd8s7tk0jyufpgejrgtg4gw5qr.
51. On the evening of May 4, 2022, after Intermediar’s confirmation of the withdrawal that same morning, and after confirmation of the separate Escrow.com transaction which had verified Dikian’s identity, VPN wired Dikian 6.27 Bitcoin, which was worth $250,000 at the time of sending, from VPN’s Coinbase Pro Account, verified by the transaction hash: bc63bcff3eb86ae1dbfbf035ef51d6594d9d6d3b372d30f1038427e227c920aa.
52. Before sending the full amount, VPN sent a test transfer of .0001 Bitcoin, which Dikian confirmed receipt of via email, and verified by the transaction hash: 935dc7ef6f55ee0cd4a1159ef367324824ef1ccf239019154672e1630 cdaa81b.