private keys of what? epik doesnt store crypto keys
Private keys have been an essential component of cryptography since long before cryptocurrency came about. They're used for everything from authenticating with core infrastructure to securing VPNs to SSL/TLS certificates.
If present (I haven't checked), that's probably the least concerning type of private key in the leak. It appears to contain private keys for SSH authentication as well as for SSL/TLS certificates.
Theoretically, if the SSH private keys are valid and protected with weak passwords (or no passwords), the attacker could've moved laterally within Epik's infrastructure: they probably would've been able to get into live systems using data from the backup. However, if they did manage to do so, they haven't shown their hand yet.
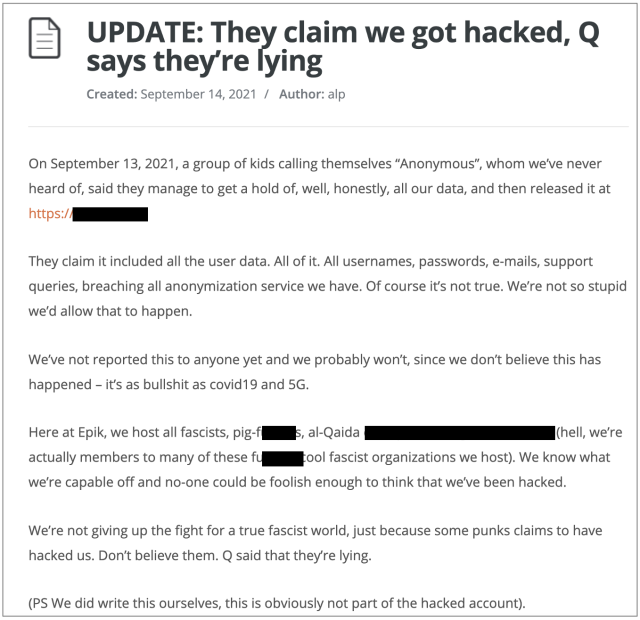
Not much has come from Epik, and the few statements certainly do not seem to acknowledge the seriousness of the situation IMO.
If the attacker has withheld data or is still in Epik's infrastructure, I'm concerned that Epik downplaying the seriousness may lead to further damage. Self-proclaimed hacktivists often seem to go that route.
The reason is that any Company is on the list for the next breach and, as a consequence of what happened, it is very unlikely that Epik will be again the next on this list.
They have received their vaccine dose. Now they're suffering for side effects, but for long time they will be immunized.
I like your optimism! I have no doubt Epik will do their best to learn from this, but it may take time for them to recover. At the moment, we're stuck in a period of uncertainty: we don't know the extent of the damage, and it's likely that Epik doesn't know yet, either. That's important to consider when doing your risk assessment and determining the best course of action.
I would also like to see other registrars learn from this, but that may be asking too much.
Human beings, who are almost unique in having the ability to learn from the experience of others, are also remarkable for their apparent disinclination to do so.
― Douglas Adams