So I was checking my emails this morning and I decided to check the spam folder (you should do this in case potential leads have been routed to spam - has happened to me in the past!). At the top of the pile I noticed an email from CEO@Federal / com. Now, I would not normally be enticed to open an email from Spam that I knew nothing about but the domain sounded too good.
I opened the email and as per usual I was being told I am the beneficiary of a large sum of money from 'Dallas Federal Bank' - ok now I knew it was a bullshit. However, I was surprised to see spam coming from such a good quality domain. Federal.com must be worth 5 figures right or at the very least 4 figures?
I also clicked the actual sender contact name to show the actual email address as sometimes the name shows a different email address but when you click into it the underlying address is a convoluted string of letters and numbers at a crap domain name. For this one it does show the email address as CEO@Federal / com.
My question is, does this mean the email was actually sent from this domain or is there some way to spoof the actual email address it self when sending an email? Why would anyone send spam / scams from premium domain name - maybe the answer is that a good domain name means more people are caught out?
Your thoughts please.
Here is a screenshot of part of the email itself:
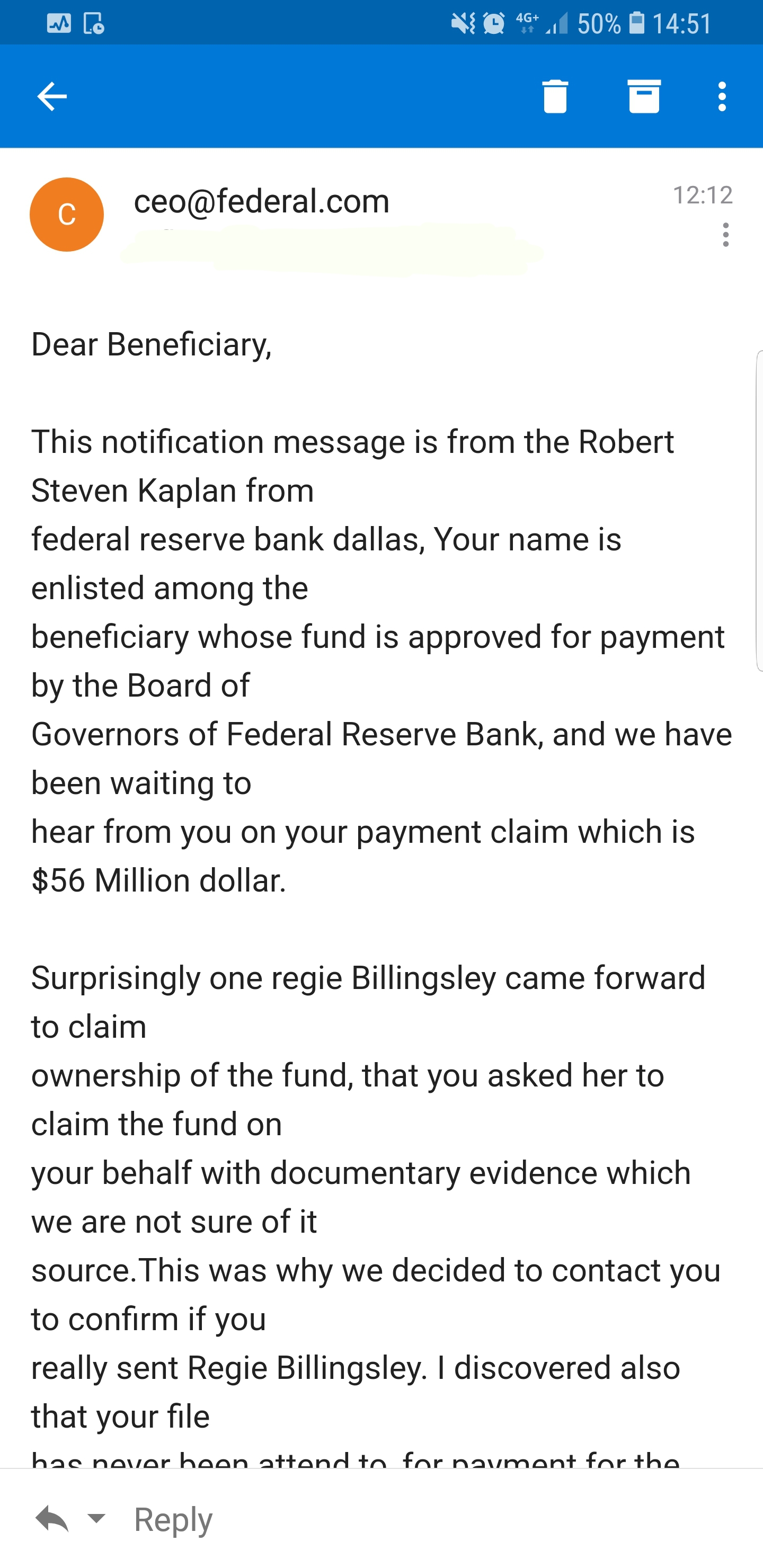
thanks,
CK!
I opened the email and as per usual I was being told I am the beneficiary of a large sum of money from 'Dallas Federal Bank' - ok now I knew it was a bullshit. However, I was surprised to see spam coming from such a good quality domain. Federal.com must be worth 5 figures right or at the very least 4 figures?
I also clicked the actual sender contact name to show the actual email address as sometimes the name shows a different email address but when you click into it the underlying address is a convoluted string of letters and numbers at a crap domain name. For this one it does show the email address as CEO@Federal / com.
My question is, does this mean the email was actually sent from this domain or is there some way to spoof the actual email address it self when sending an email? Why would anyone send spam / scams from premium domain name - maybe the answer is that a good domain name means more people are caught out?
Your thoughts please.
Here is a screenshot of part of the email itself:
thanks,
CK!
Last edited:





