- Impact
- 1,570
Mods not sure this is the correct forum, please feel free top move it if I have chosen the wrong Forum.
Hello,
First off, I am not affiliated with TheDomains.com at all. It is and always was Mike Berkens site. Raymond Hackney @equity78 is a huge part of TheDomains.com now since MB kinda retired.
So, I was off of work today.. I should have done many things, ran errands, put some domains in auction, domain management, wrote in my own blog (which I have the hardest time ever doing), crypto coin movement since market moved, and a long honey-do list, etc.
I start off my day, looking at the domain blogs, and of course checking my Twitter account. I notice that TheDomains Twitter account got hacked. That kind of pissed me off. Nobody should be able to do that. Some people were trying to help tweet to people to report this hack to Twitter, just press the gear icon, etc. Well, my desktop twitter didnt have one so I created a screenshot showing how to report it from desktop set-up.
Twitter support blows. I am sure that so many fans of The Domains have reported this, and still no help. The knucklehead holding the twitter account for ransom still has full control of the site. This only goes to show the rest of us that have many less followers, that if we ever get hacked, we will never get our accounts back.
So, this starts bothering me. I know Ray for almost 10 years now. Mike Berkens had my favorite portfolio of any big time domainer ever, before selling it. Almost got to meet Mike when in Ft. Lauderdale a couple years ago. Just seems like a very cool guy. I have TONS of respect for TheDomains.com and Mike and Ray.
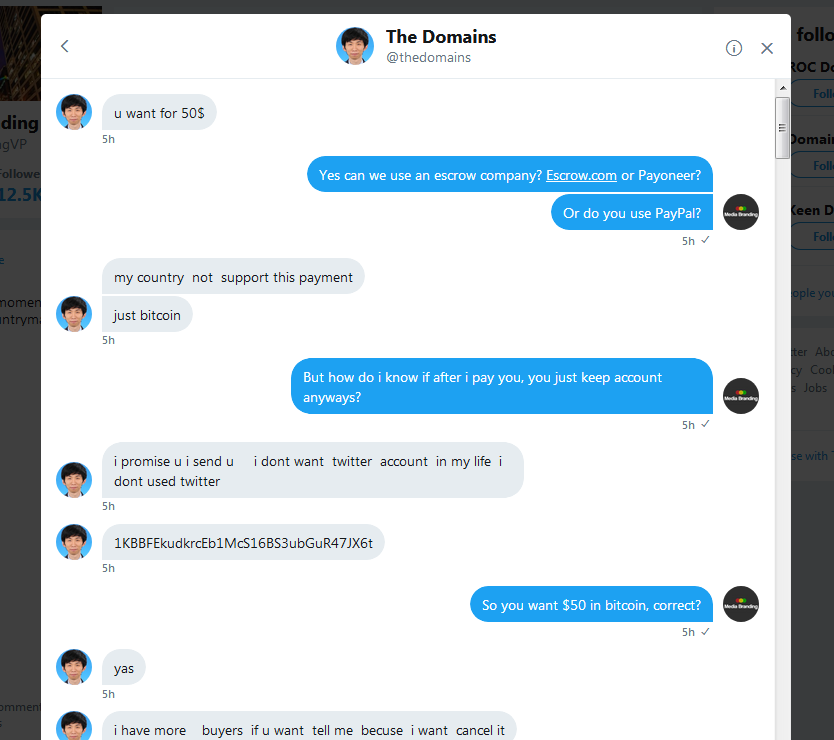
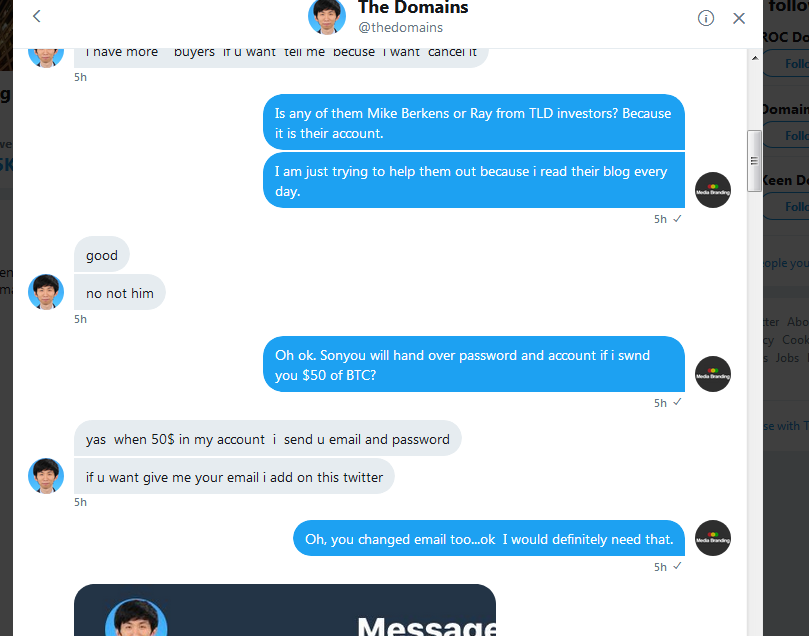
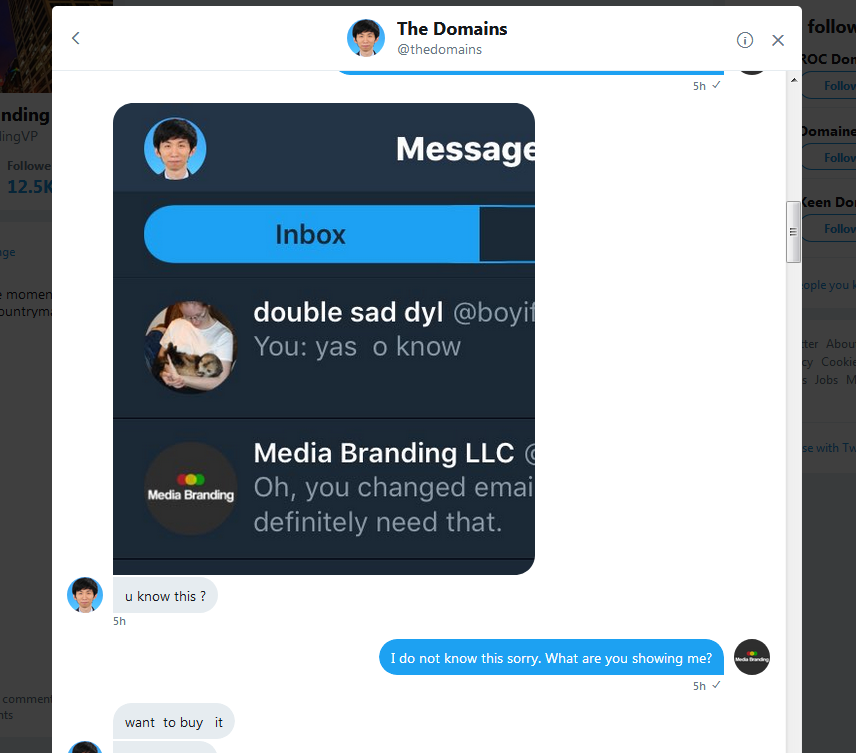
Ok so, I see this knucklehead hacker tweeting on that account. At one time, he asks for $50 in Bitcoin to get account back. I tweet that I will pay it to get it back to them.
Then he direct messages me.His tweets sounded childish, but his DM's sounded much more civil. So, I feel like I am dealing with a guy down on his luck and he is a hacker, sure I will give him the $50 to get the account back to Mike and Ray.
Thats where I F-ed up.
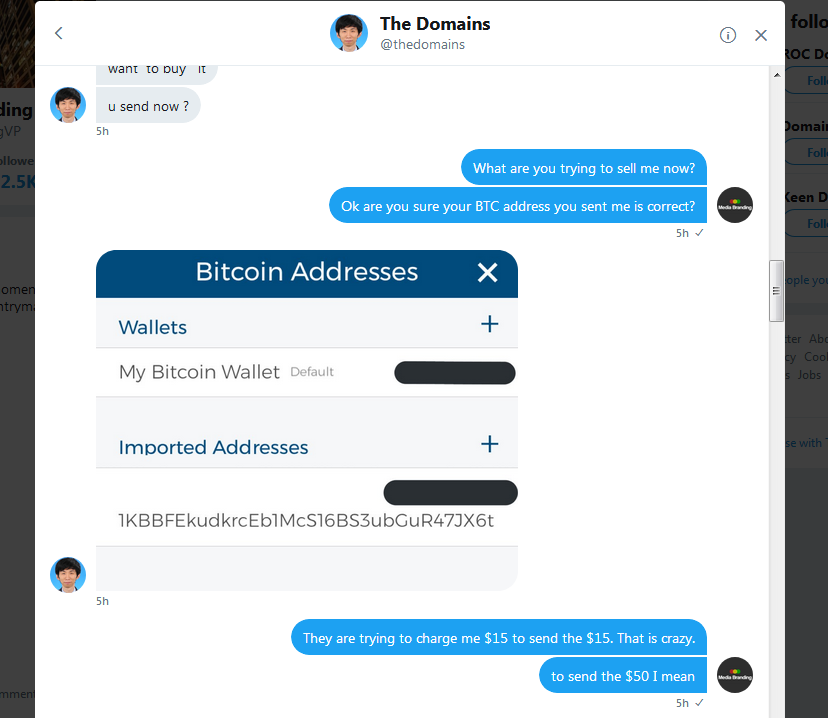
So, I sent him $50 in Bitcoin from my Bittrex along with the $15 fee thinking he was going to turn over the account. Of course, he didn't
Now, you may call me an idiot, and I get it. I do feel embarrassed. Based on the DM's I really felt like I could fix this. The money was not too big of an issue to me considering the knowledge I have gotten from Mike on TheDomains.com for free for all of these years, and Ray has done 100x more than $50 worth for me in the past 10 years as well. So this could have been a great ending but unfortunately not.
This is where you come in.
Can anyone find this guy? I know there are some brilliant people who frequent this forum and I think I got a lot of information from this scumbag. A couple members I have seen here who have done some great investigative work... @Grilled @promo anyone else that may be able to help, that would be extremely cool!
I am gonna eventually post my whole DM conversation here thru screenshots. I have his Bitcoin address and some text address screenshot that may be helpful. I don't know why, but I am angered by this big time like it is my own site even though it isn't.
Thanks,
Vito
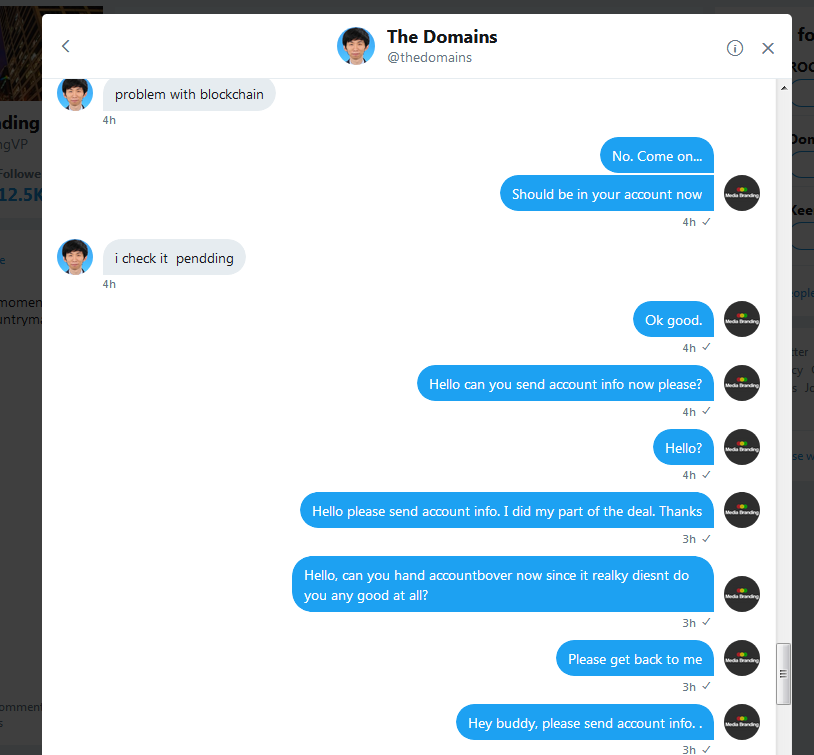
Ok I think I captured entire conversation
Here goes...
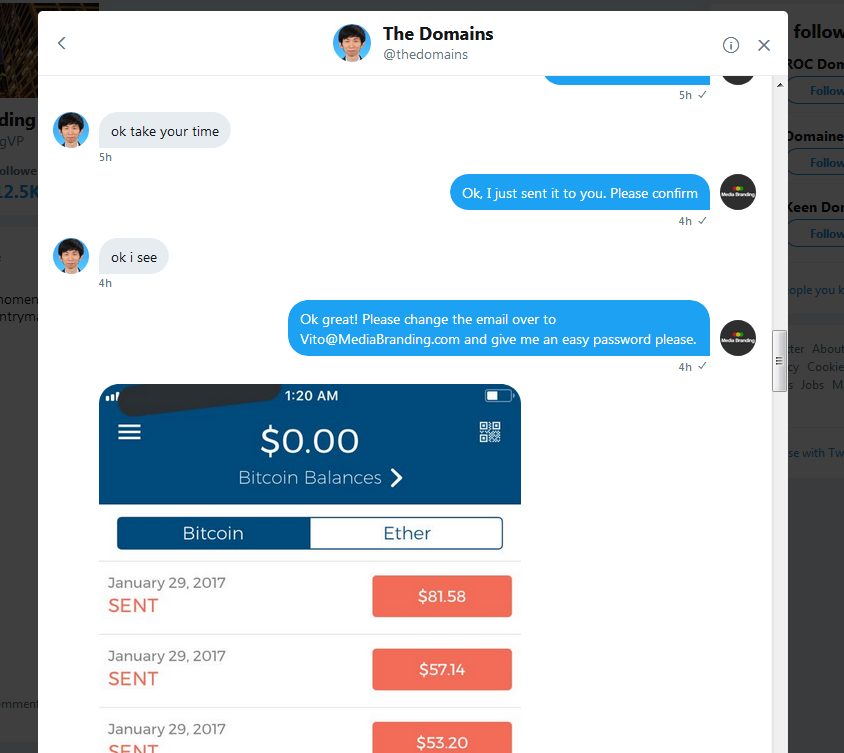
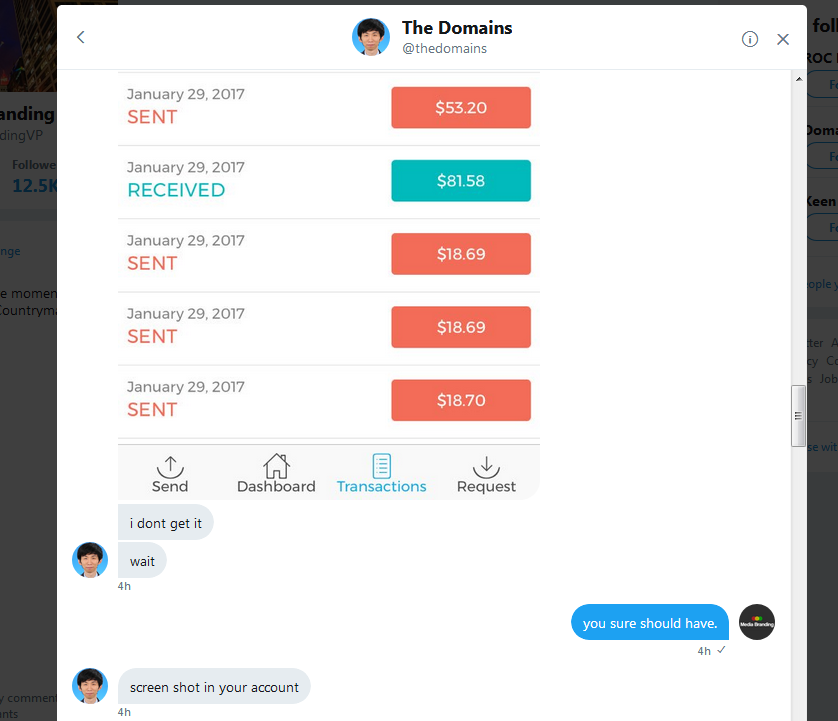

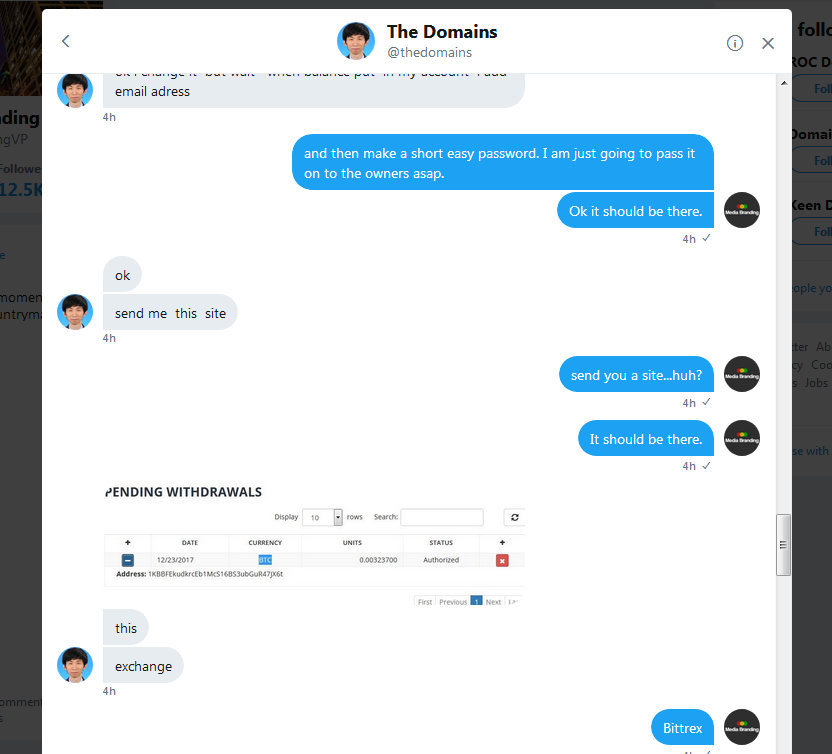
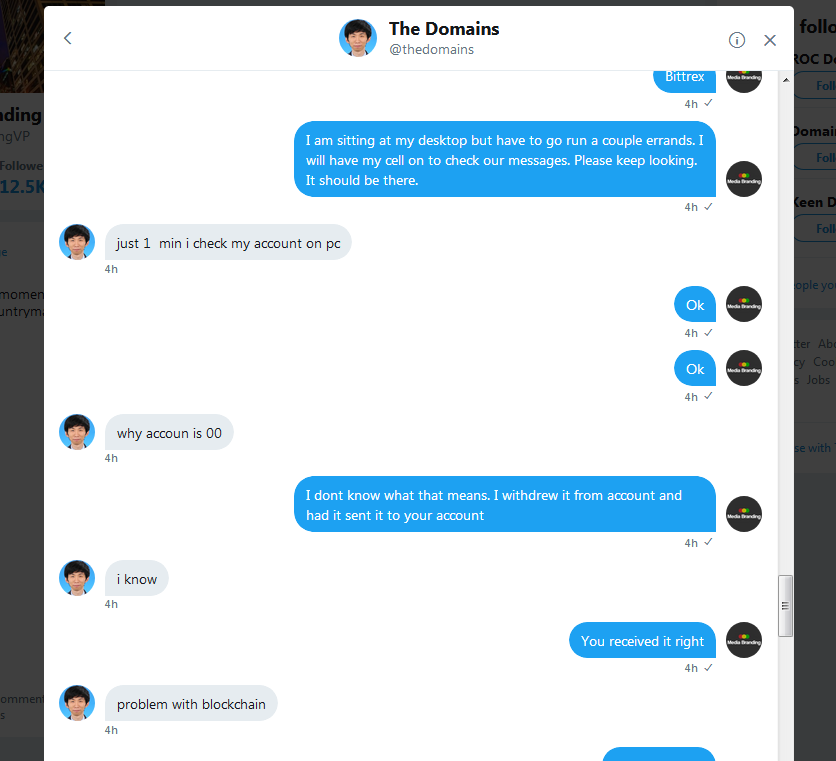
Hello,
First off, I am not affiliated with TheDomains.com at all. It is and always was Mike Berkens site. Raymond Hackney @equity78 is a huge part of TheDomains.com now since MB kinda retired.
So, I was off of work today.. I should have done many things, ran errands, put some domains in auction, domain management, wrote in my own blog (which I have the hardest time ever doing), crypto coin movement since market moved, and a long honey-do list, etc.
I start off my day, looking at the domain blogs, and of course checking my Twitter account. I notice that TheDomains Twitter account got hacked. That kind of pissed me off. Nobody should be able to do that. Some people were trying to help tweet to people to report this hack to Twitter, just press the gear icon, etc. Well, my desktop twitter didnt have one so I created a screenshot showing how to report it from desktop set-up.
Twitter support blows. I am sure that so many fans of The Domains have reported this, and still no help. The knucklehead holding the twitter account for ransom still has full control of the site. This only goes to show the rest of us that have many less followers, that if we ever get hacked, we will never get our accounts back.
So, this starts bothering me. I know Ray for almost 10 years now. Mike Berkens had my favorite portfolio of any big time domainer ever, before selling it. Almost got to meet Mike when in Ft. Lauderdale a couple years ago. Just seems like a very cool guy. I have TONS of respect for TheDomains.com and Mike and Ray.
Ok so, I see this knucklehead hacker tweeting on that account. At one time, he asks for $50 in Bitcoin to get account back. I tweet that I will pay it to get it back to them.
Then he direct messages me.His tweets sounded childish, but his DM's sounded much more civil. So, I feel like I am dealing with a guy down on his luck and he is a hacker, sure I will give him the $50 to get the account back to Mike and Ray.
Thats where I F-ed up.
So, I sent him $50 in Bitcoin from my Bittrex along with the $15 fee thinking he was going to turn over the account. Of course, he didn't
Now, you may call me an idiot, and I get it. I do feel embarrassed. Based on the DM's I really felt like I could fix this. The money was not too big of an issue to me considering the knowledge I have gotten from Mike on TheDomains.com for free for all of these years, and Ray has done 100x more than $50 worth for me in the past 10 years as well. So this could have been a great ending but unfortunately not.
This is where you come in.
Can anyone find this guy? I know there are some brilliant people who frequent this forum and I think I got a lot of information from this scumbag. A couple members I have seen here who have done some great investigative work... @Grilled @promo anyone else that may be able to help, that would be extremely cool!
I am gonna eventually post my whole DM conversation here thru screenshots. I have his Bitcoin address and some text address screenshot that may be helpful. I don't know why, but I am angered by this big time like it is my own site even though it isn't.
Thanks,
Vito
Ok I think I captured entire conversation
Here goes...
Last edited:






